This video explains the digital currency mechanism (configure).
And it gives you a clearer idea of the true meaning of the possession and send and exploration of digital currency.
I’ll start with a brief overview of the first and advanced about the meaning of Alpetkoan.
At Alpetkoan Johrh- is a digital file containing accounts and funds, and thus looks like a ledger.
And keeps every computer in the network Alpetkoan a copy of this file.
These figures do not represent anything in the real world.
These numbers have a value only because people
Ready to deal in goods and services in exchange for a higher number in their accounts.
And they believe that others will do ideals,
Where these numbers have a value only because we believe in it.
This is no different from any other paper currency.
If you want to send money, you want to broadcast in the network that you want to decrease the number in your account
And the figure rises in the recipient’s account.
Nodes are implemented (or computers) in the network Alpetkoan this transaction is in the version of the ledger
Then send the deal to another contract.
In addition to the above, some basic safety procedures based on mathematics, and that’s all of it!
It is a system that allows a group of computers to maintain ledger accounts.
This may seem similar to the way in which the Bank holds ledger accounts.
But the existence of the ledger when a group of people rather than one institution leads to a set of important features.
For example, you do not know anything about your position only when dealing with the bank.
In Alpetkoan, everyone knows about all transactions that occur.
You can trust your bank, or at least you can be paid if a bug has occurred.
In Alpetkoan you are dealing with anonymous strangers so you should not trust anyone!
Alpetkoan system was designed so tightly did not need any confidence!
Where special protection everything in the system mathematical equations.
And the rest of the video will explain in detail how can configure
To allow a group of strangers to organize financial transactions for each other.
Simply put, if it wants to “Alice” to send money to “Bob”
Send a message containing the accounts and the amount of money you want to send.
“Send 5 pieces of Alpetkoan from Alice to Bob.”
Speaking after each node receives the message copied from the accounts book
And then re-send this message to others.
But how the contract to know that this request is false.
Ie that the account holder is the one who sent the message.
You need some sort of rules Alpetkoan passwords that allows you to send money
This is called password digital signature.
And it looks like it is written signature proves that the demand is false
But it does so through a mathematical algorithm to prevent copying or fraud in the electronic Kingdom.
This differs from the use of the word fixed password,
Every deal you need a digital signature characteristic is different.
Remember that you’re dealing with strangers so you do not show them any password Vinsguha or use them elsewhere.
Digital signature by using two different keys works but linked.
The first is a secret key to create a digital signature
And the other key public can be used to verify the authenticity of the signature.
It considered that the secret key is the real password
The digital signature is the broker confirms that you have the password without having to show.
Public key is used as the address of the addressee in Alpetkoan.
When you send money to someone you send money to his key public.
To send money, you have to prove that you are the real owner of the public key that pulled him money.
To do so you have to create a digital signature by using the message container on the deal and the secret key.
Can other contract in the network
To use this signature in another function to verify that they are compatible with your key public.
And allow the underlying mathematics behind the digital signature to confirm that the sender has the secret key without having to see it.
Because the generation of digital signature depends on the message,
The digital signature will be unique in each transaction.
And therefore it can not be reused for another deal.
This reliance on the message means that no one will be able to modify the message while sending in the network.
Because any modification in the letter will make a false signature.
Underlying mathematics behind this highly complex,
And I will not try to explain it in detail now
But I’ll give you some words that you can begin to look for:
ECDSA and mathematical trap door.
And I will explain more at the end of the video.
So far we know that the digital signature is used to prove that the deal is forged,
But I exaggerated the simplification of the mechanism that tracks through which the contract changes in account balances.
In fact, the contract does not store account balances at all.
But if you do not store the amount of money owned by each person,
How do you know they have enough money to submit it to others?
Instead of storing balances.
Proving ownership of enough money by linking them with previous deals.
And I will explain how this happens.
To send Alice 5 pieces to Bob,
They must refer to other transactions which received five pieces or more.
These other deals are called “Palmdjulat”.
Whereupon the other nodes to verify these inputs to make sure that this money is not received
And that the total received greater or equal to five pieces.
Let’s look at a real deal to see how this happens.
This transaction refers to a total of six revenues 139.6 pieces.
Note that the output contains two lines.
The first restores the overflowing of the funds needed to the sender.
Where the rule states that all the money in one of the inputs must be used in the whole deal.
If you want to send the amount of money is not equal exactly the amount of money in the inputs that I referred to,
You have to send any money to spare yourself again.
And cross-reference to the inputs transferred ownership Alpetkoan in the chain-like,
Where the legitimacy of a transaction depends on the legitimacy of previous deals,
But how do you trust the legitimacy of these previous deals?
Answer: You can not!
And you have to verify the legitimacy of its revenues as well.
In fact, after the inauguration of the program portfolio Alpetkoan for the first time,
The program loads each deal has since the beginning Alpetkoan
And then verify the legitimacy of one after the other until you can verify the legitimacy of the first deal was.
Remember that you are dealing with strangers
Therefore, it is necessary to verify the legitimacy of each transaction yourself.
These scientific take more than 24 hours
But you will not need it more than once.
And after using one of the deals once
This is the deal and disbursed can not be used again.
And only one of them can be used one Mdjulath several times to refer to it in several deals.
So the contract when you check the legitimacy of the transactions to ensure that its revenues have not acted before.
To be frank, and for each income
The contract realized from all previous transactions to make sure that this intake was not distracted by
This may seem a waste of time
Because there are more than 20 million deal now,
But it is quick because of an index containing transaction is disbursed.
If instead retain the contract book of accounts,
They can track the huge list of deals.
And owning a digital currency (configure)
Means that there are deals to indicate your name on this list has not yet acted
(Ie, did not refer to it Kmadjulat in other deals).
One important and this property model results
To know your digital currency
Needs to pass through each transaction has
Then collect all Mdjulatk is disbursed.
And add to this important note:
The system can support more complex than just sending money from someone else’s trades.
You may have noticed the line is incomprehensible in the deal that we presented previously came out.
Where the output is like the issue to be solved, rather than be a simple container consignees addresses.
Instead of sending the money to be similar to sending the message,
Sending money in Alpetkoan like putting money in a public safe
And the issue of math lock must be resolved until you open the safe,
Know the question of mathematics special programming language,
And with that they are specifically designed to be solved by a single owner of the public key,
There are many other possibilities.
For example, we may need to signatures out of three to pass based on ensuring a third party transaction.
And another example is the first deal has ever contained the question of which anyone can be solved.
Most of the governor Alpetkoan hide from you this class code
But you can be programmed with your own program that this has something to risk.
More than 2,600 pieces have disappeared because of errors in the addresses in a range of deals.
This emphasizes is important when dealing with Alpetkoan,
Since you can not resort to a bank or credit card company
Any errors by the user may lead to a permanent loss of digital blocks,
This loss is not only limited to your account
It is the loss of a full Alpetkoan economy.
If you lose your secret
Any funds linked to the corresponding public key will disappear forever.
Since people often lose their keys
For reasons such as hard disks crash and not back up,
It means that the currency Alpetkoan will shrink with time.
Before I talk about the latest technology and believes in the work of Alpetkoan is (exploration),
I want to mention a few points about privacy when dealing Balbtkoan.
If Alpetkoan entered through a network (Tor) that hide the IP address of thy,
You can use Alpetkoan without showing anything other than the public key.
To avoid the one to track all your transactions
(Remember, all transactions are stored on all computers!)
You can generate a new public key for each incoming deal.
However it can be linked to these public keys accidentally.
In the deal we have shown previously used six other deals as sources of money,
And that with all these inputs received to different addresses
They are all linked to the transaction.
And the sender has demonstrated its ownership of all these titles
Through the provision of electronic sign necessary to decode the lock each.
The researchers used these links to study user behavior currency Alpetkoan.
You may think that generate a public key to receive the funds may eventually lead to reveal the true identity,
But even this step are confidential.
And it can be done without an internet connection!
Where simply press the custom button in the wallet program
And the software will generate a public key and a special two new.
Since there are many possibilities for these titles,
There is no need to make sure that no other person has the same title.
Compare this with the registration service for e-mail
Where most of the names that you might consider them to be used in advance.
In fact, if you can guess someone else will own all his money key!
This is the number of all possible possibilities for addresses Alpetkoan.
These massive numbers in several ways to protect Alpetkoan system.
And it is useful to try to imagine the extent of magnitude,
Some estimated the number of grains of sand on Earth by 7.5 million trillion,
Now imagine that every grain of sand is another land full containing other sand,
With this figure will remain much lower than the number of possibilities Alpetkoan addresses.
Flanl_khas what we have learned about Alpetkoan security now.
By ensuring the validity of the electronic signature.
We know that the rightful owner is the only one capable of sending the deal
To verify that the sender has enough money to spend.
Check every income indicated to make sure that it is not an expense
But there is still one loophole in the system
This makes “verify that the transaction is disbursed” is not trusted.
And this gap related to the order of the transaction.
As the transaction moves from one node to another over the network,
There is no guarantee that the order in which these deals received is the same as the order in which it was established.
Do not trust registered on the transaction time
Because the owner of the deal can easily lie about the time of the establishment of the deal.
And therefore we have no way to know whether a transaction was established before the other
This opens the door to fraud.
A user can be cunning like Alice sends a deal that sends them his money to Bob,
Bob and then wait until the goods shipped to him,
And then sends another deal which refers to the same intake and return the money to himself.
Because of the differences in the speed of transmission of the message,
You will receive some of the network nodes in the second letter (in which the money was transferred to itself)
Before the message where the money is spent on Bob.
And when you reach the deal with Bob would be considered illegal
As it tries to re-spending one earnings.
Bob Vijsr this both of his goods and his money.
The result would be contrary to within the network whether or not Bob owns this money
Because of the absence of a way to prove that one of the deals came first.
And therefore there must be a way to allow for the entire network to agree on the order of a transaction,
And it is complex in a decentralized system.
The solution in the Alpetkoan system is a smart way to ensure the protection and determine the order of occurrence of transactions
And through some kind of racing sports.
Arranges Alpetkoan system deals placing them in groups called blocs,
And then connects these blocks with each other in so-called chain blocks.
Note that it is different from the chain of transactions that we talked about previously.
Where he used a series of blocks to arrange deals,
While serving the chain of transactions to track the ownership of the funds.
It is noteworthy in each block to the previous block,
And this is what makes it one of the blocks other precedes chronologically.
Where you can keep track of these signals about the past until you reach the first mass of transactions occurred.
Ntabbar that deals in one block occurred at the same time.
And called the deals that did not fall within the block after transactions is ranked or undocumented.
Any node can be several deals not documented in the mass rally
Then it suggests this block on the rest of the nodes in the network to be the new cluster in the chain.
Because several people can establish several blocks at the same time,
There are several possible new options as a bloc.
How can the network to decide which blocks are the next in the series?
We can not rely on the order of receipt of the blocks,
As we explained earlier for deals,
These blocks can reach different in the different nodes in the network order.
Part of the solution is that each block must contain a distinctive mathematical solution to the issue.
Where computers are used text content in the cluster to add random numbers Speculative
To create the so-called “retail encrypted”
Until you find the result is less than a specified value.
Continued retail creates short as a result of any text, whatever its length,
In our case the result is a record length of 32 bytes.
Here are some examples of retail user continued in Altbekoan SHA256 system
Notice how much output changes after adding one point at the end of the third example.
No one can predict the output never
Consequently, the only way to find a particular output is to carry out a random guess.
This is like trying to guess the password to lock.
You may be lucky in the first attempt,
But you need a few guesses average.
In fact, it may take a normal computer a few years to find true guesswork solves mass.
All computers operate on a network Alpetkoan to guess the numbers,
And thus find the solution takes an average of ten minutes.
Broadcast the first to find a solution to the issue of mass mathematics
And group transactions contained therein will become a new block in the chain.
Random sports issue lead to a variation of the times when people find a solution
Which reduces the probability to find two to resolve the issue at the same time.
But several blocks at the same time may sometimes be resolved
Which leads to the presence of several possible branches.
In this case, you have to build on the first block you receive.
Others may receive the blocks in a different order
And each of them will be built on the first block received.
And this node resolved when someone resolves the next block.
And the base should always rely longer series are available.
Make the possibility of solving math blocks at the same time weak.
The probability of occurrence of several consecutive times weaker.
And the result is that a series of blocks settle down quickly,
This means that all agreed on the order of the blocks added to the end of the chain.
Ambiguity at the end of the chain a significant impact on security transactions.
For example, if you signed your deal in the short section in the series will lose its place in a series of blocks.
This means that they will return to box undocumented transactions,
It later becomes a new block components.
Unfortunately, the deal opens up the possibility of losing their place in the chain to the door to the spending multiplier attack
Which was the first reason we invented a system arrangement.
Let’s see how it works spending multiplier attack in the system that described now.
The conman (Alice) to send money to Bob.
Bob is expected to document the deal in a series of blocks and then ship the goods.
Now, and because the contract always choose the longest chain,
If it can not generate the longest series in which the deal is replaced with Bob another deal with someone else,
Erased his money from the chain.
Bob will return a deal in principle to non-documented transactions.
But since the deal is not replaced it with another which has spent the same intake,
Bob contract deal will be considered invalid, because they rely on income already spent.
How prevents the ranking system is not fool Bob?
You may think that you can not pre-calculated series of blocks to the proposed network in a timely manner,
But sports matter in each block to prevent such.
Should we look more deeply on the encrypted hash continued that we talked about in advance in order to understand exactly why.
As I mentioned previously,
Cluster solution depends on trying to make the encrypted hash of the block output of less than a certain value.
And do so through the experience of different random numbers at the end of the block.
And output becomes a sign marked after be found this block (fingerprint).
And change one character in the cluster will make retail output completely different,
And so as we saw earlier when we add point.
Using retail output, or footprint, to refer to the previous block.
And therefore it can not replace the block in the middle of the chain because the hash value of the new block will vary,
And the signal in the next block will not refer to it later.
And the output is self-evident, but more importantly, one can not solve the block before we solve the bloc that precede them.
And the reference to the previous block is part of the cluster text that enters the retail continued,
And any change in it will need to be re-solution again.
And to return to Alice,
We are not aware can not calculate a branch in advance.
You can begin to dissolve the block only if the cluster that you want to build on it Solved, and the retail value of the known.
And therefore they are in a race with the rest of the network until the goods shipped Bob,
And it is the time you want it not display the longest branch.
And ask the question last one
And you are Can not precede all if you own a computer supernatural speed,
Or perhaps full of computer room.
Even if possessed thousands of computers will not be able to profit from the race and mass solution,
Because they do not race alone computers,
But it raced the entire network.
This is like a lottery game.
Can use thousands of computers,
Or to buy thousands of lottery cards,
But even if it did, the possibility of profit for someone else remains high.
It has to have more than half of computational power for the entire network
To be her chance to dissolve the bloc by another person 50%.
And it should have much more in order to have the possibility to solve several sequential blocks before the rest is greater.
Protect deals in the series of blocks through a sports race,
This race puts forward against the rest of the entire network.
And result in the creation of new blocks over the old that the old blocks in the chain more secure.
And the attacker must be preceded by the network for longer
To succeed spending multiplier attack by replacing old ones block.
The system exhibition spending multiplier attack near the end of the series,
For this reason is advisable to wait until added a few new blocks
Before it is considered the process of receiving final funds.
One final note series blocks before I begin to explain another issue for Alpetkoan system.
What is surprising that all the above and I explained does not need any confidence.
If you receive information from strangers on the network,
You can be sure that the blocks yourself solutions are correct.
Because tough math problems, you are sure that there is no striker is able to manufacture himself.
The existence of solutions proved to be caused by the computational capacity of the entire network.
After that we talked about the mechanism of sending money through digital signature and chains deals,
How protects the order of these deals in a series of blocks,
Let’s talk about another topic: where it comes from coin Alpetkoan?
You have to refer to an old deal where you’re the recipient before you can send money,
But how these funds enter into the ownership chain at the beginning?
The way through which generate and distribute the pieces at random,
Award is to give each of finding a solution to the mass.
For this so-called solution blocks “prospecting”
With the primary aim is to document transactions and protect the chain blocks.
Cut the prize every four years to half and in the end will not be created any new cut,
There will be about 21 million pieces in the end.
Remember that you can send the equivalent part of a million percent portion of the piece,
And thus the limited number of pieces on our ability to use it will not affect.
When the distribution of the awards depends,
What are the incentives that will pay prospectors to handle deals?
You can prospector receive with their prize any fees on deals
Which can optionally be present within these transactions.
Prospectors currently adds deals without fees in the blocks
Because their primary goal is the prize after a mass solution,
In the future, transactions will be dealt with mostly by fees attached to them,
The deals that do not carry fees Vsijahlunha often.
And therefore will not be sending money in free Alpetkoan,
But we hope to be cheaper than the fees levied on credit cards.
As I mentioned earlier, it would take a normal computer and the average number of years to resolve the block,
And thus the chance of one individual to resolve any block before the rest of the network (which normally takes ten minutes) is very low.
For a stable financial Ward,
Many people join groups called Mines
Which cooperate to solve the mass and resources are distributed based on the amount of participation.
And is similar to that lottery cooperative groups,
Except that some of these mines is very large, and make up more than 20% of the computers on the network.
The presence of these large mines have a significant impact on safety.
As we mentioned earlier, one attacker can not solve a series of sequential blocks before the rest of the network,
But this becomes possible, and the probability of its occurrence increases the more computing capacity of the attacker compared with the rest of the network.
And it has already managed one of the mines, union Alpetkoan, to replace the six blocks of sequential alone,
It identifies the number of its affiliates voluntarily and in order to prevent the collapse of confidence in network Alpetkoan.
Even with a high computing power,
Whenever the deal earlier in the series, the more change more difficult by the attacker.
Currently it recommended that you wait for one block, or get a closer one, before the transmission is considered final.
And for the great deals, wait six blocks at least.
And with the ability of union Alpetkoan six sequential blocks solution you’ll probably have to wait more.
The blocks are designed so that you need ten minutes to solve,
So you have to wait a full hour to solve 6 new blocks.
If you compare it with the few seconds it takes to send a deal via credit card,
You’ll find all this waiting period to document the deal is troublesome,
But remember that credit card users can call steal their card after several months
And to restore their money from the merchants,
And therefore Alpetkoan much faster than the point of view of the merchant.
The choice of ten minutes was randomly,
But too little will lead to instability,
And long time will lead to the postponement of documenting transactions.
And join with the largest number of computers to the network,
With the hardware design software dedicated to the exploration,
Will decrease the time needed to resolve the block.
And to compensate for it,
Re-evaluation of all programs Alpetkoan difficult math problems every two weeks
So it takes ten minutes to solve.
Conversely, there is another digital currency called the Aatkoan was able to operate time of 2.5 minutes for each block.
In summary, Alpetkoan is a digital coin protected mathematics
And it works to save users on the network.
The digital signature gives individuals the right to conduct transactions,
And transferred ownership across the chain of transactions,
And saves the sequence of occurrence of transactions arranged in a series of blocks.
And a request to resolve the issue of mathematics for each block,
Put the attackers in the competition can not be Arbhoha against the rest of the network.
The future Alpetkoan many creative ideas,
Such as preventing government intervention and reduce financial secrecy and transfer fees.
There are many challenges faced, such as the difficulty of sharing Alpetkoan with other currencies,
And was a classification refuge for illegal acts and tax evasion,
So governments may try to prevent them.
In addition, the mathematics race series which protects the blocks consumes a large amount of electricity.
If you want to read a written copy of the video
You can drop my blog,
imponderablethings.com
The Code contains additional explanations for the underlying mathematics behind the digital signature and encrypted hash that support the system.
And it gives you a clearer idea of the true meaning of the possession and send and exploration of digital currency.
I’ll start with a brief overview of the first and advanced about the meaning of Alpetkoan.
At Alpetkoan Johrh- is a digital file containing accounts and funds, and thus looks like a ledger.
And keeps every computer in the network Alpetkoan a copy of this file.
These figures do not represent anything in the real world.
These numbers have a value only because people
Ready to deal in goods and services in exchange for a higher number in their accounts.
And they believe that others will do ideals,
Where these numbers have a value only because we believe in it.
This is no different from any other paper currency.
If you want to send money, you want to broadcast in the network that you want to decrease the number in your account
And the figure rises in the recipient’s account.
Nodes are implemented (or computers) in the network Alpetkoan this transaction is in the version of the ledger
Then send the deal to another contract.
In addition to the above, some basic safety procedures based on mathematics, and that’s all of it!
It is a system that allows a group of computers to maintain ledger accounts.
This may seem similar to the way in which the Bank holds ledger accounts.
But the existence of the ledger when a group of people rather than one institution leads to a set of important features.
For example, you do not know anything about your position only when dealing with the bank.
In Alpetkoan, everyone knows about all transactions that occur.
You can trust your bank, or at least you can be paid if a bug has occurred.
In Alpetkoan you are dealing with anonymous strangers so you should not trust anyone!
Alpetkoan system was designed so tightly did not need any confidence!
Where special protection everything in the system mathematical equations.
And the rest of the video will explain in detail how can configure
To allow a group of strangers to organize financial transactions for each other.
Simply put, if it wants to “Alice” to send money to “Bob”
Send a message containing the accounts and the amount of money you want to send.
“Send 5 pieces of Alpetkoan from Alice to Bob.”
Speaking after each node receives the message copied from the accounts book
And then re-send this message to others.
But how the contract to know that this request is false.
Ie that the account holder is the one who sent the message.
You need some sort of rules Alpetkoan passwords that allows you to send money
This is called password digital signature.
And it looks like it is written signature proves that the demand is false
But it does so through a mathematical algorithm to prevent copying or fraud in the electronic Kingdom.
This differs from the use of the word fixed password,
Every deal you need a digital signature characteristic is different.
Remember that you’re dealing with strangers so you do not show them any password Vinsguha or use them elsewhere.
Digital signature by using two different keys works but linked.
The first is a secret key to create a digital signature
And the other key public can be used to verify the authenticity of the signature.
It considered that the secret key is the real password
The digital signature is the broker confirms that you have the password without having to show.
Public key is used as the address of the addressee in Alpetkoan.
When you send money to someone you send money to his key public.
To send money, you have to prove that you are the real owner of the public key that pulled him money.
To do so you have to create a digital signature by using the message container on the deal and the secret key.
Can other contract in the network
To use this signature in another function to verify that they are compatible with your key public.
And allow the underlying mathematics behind the digital signature to confirm that the sender has the secret key without having to see it.
Because the generation of digital signature depends on the message,
The digital signature will be unique in each transaction.
And therefore it can not be reused for another deal.
This reliance on the message means that no one will be able to modify the message while sending in the network.
Because any modification in the letter will make a false signature.
Underlying mathematics behind this highly complex,
And I will not try to explain it in detail now
But I’ll give you some words that you can begin to look for:
ECDSA and mathematical trap door.
And I will explain more at the end of the video.
So far we know that the digital signature is used to prove that the deal is forged,
But I exaggerated the simplification of the mechanism that tracks through which the contract changes in account balances.
In fact, the contract does not store account balances at all.
But if you do not store the amount of money owned by each person,
How do you know they have enough money to submit it to others?
Instead of storing balances.
Proving ownership of enough money by linking them with previous deals.
And I will explain how this happens.
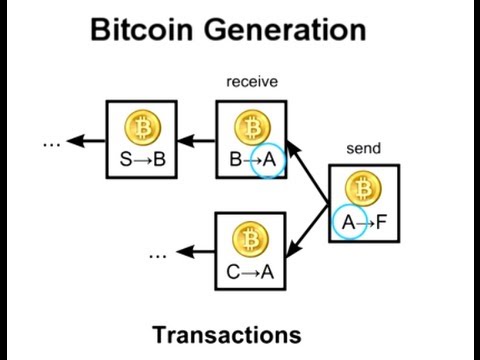
To send Alice 5 pieces to Bob,
They must refer to other transactions which received five pieces or more.
These other deals are called “Palmdjulat”.
Whereupon the other nodes to verify these inputs to make sure that this money is not received
And that the total received greater or equal to five pieces.
Let’s look at a real deal to see how this happens.
This transaction refers to a total of six revenues 139.6 pieces.
Note that the output contains two lines.
The first restores the overflowing of the funds needed to the sender.
Where the rule states that all the money in one of the inputs must be used in the whole deal.
If you want to send the amount of money is not equal exactly the amount of money in the inputs that I referred to,
You have to send any money to spare yourself again.
And cross-reference to the inputs transferred ownership Alpetkoan in the chain-like,
Where the legitimacy of a transaction depends on the legitimacy of previous deals,
But how do you trust the legitimacy of these previous deals?
Answer: You can not!
And you have to verify the legitimacy of its revenues as well.
In fact, after the inauguration of the program portfolio Alpetkoan for the first time,
The program loads each deal has since the beginning Alpetkoan
And then verify the legitimacy of one after the other until you can verify the legitimacy of the first deal was.
Remember that you are dealing with strangers
Therefore, it is necessary to verify the legitimacy of each transaction yourself.
These scientific take more than 24 hours
But you will not need it more than once.
And after using one of the deals once
This is the deal and disbursed can not be used again.
And only one of them can be used one Mdjulath several times to refer to it in several deals.
So the contract when you check the legitimacy of the transactions to ensure that its revenues have not acted before.
To be frank, and for each income
The contract realized from all previous transactions to make sure that this intake was not distracted by
This may seem a waste of time
Because there are more than 20 million deal now,
But it is quick because of an index containing transaction is disbursed.
If instead retain the contract book of accounts,
They can track the huge list of deals.
And owning a digital currency (configure)
Means that there are deals to indicate your name on this list has not yet acted
(Ie, did not refer to it Kmadjulat in other deals).
One important and this property model results
To know your digital currency
Needs to pass through each transaction has
Then collect all Mdjulatk is disbursed.
And add to this important note:
The system can support more complex than just sending money from someone else’s trades.
You may have noticed the line is incomprehensible in the deal that we presented previously came out.
Where the output is like the issue to be solved, rather than be a simple container consignees addresses.
Instead of sending the money to be similar to sending the message,
Sending money in Alpetkoan like putting money in a public safe
And the issue of math lock must be resolved until you open the safe,
Know the question of mathematics special programming language,
And with that they are specifically designed to be solved by a single owner of the public key,
There are many other possibilities.
For example, we may need to signatures out of three to pass based on ensuring a third party transaction.
And another example is the first deal has ever contained the question of which anyone can be solved.
Most of the governor Alpetkoan hide from you this class code
But you can be programmed with your own program that this has something to risk.
More than 2,600 pieces have disappeared because of errors in the addresses in a range of deals.
This emphasizes is important when dealing with Alpetkoan,
Since you can not resort to a bank or credit card company
Any errors by the user may lead to a permanent loss of digital blocks,
This loss is not only limited to your account
It is the loss of a full Alpetkoan economy.
If you lose your secret
Any funds linked to the corresponding public key will disappear forever.
Since people often lose their keys
For reasons such as hard disks crash and not back up,
It means that the currency Alpetkoan will shrink with time.
Before I talk about the latest technology and believes in the work of Alpetkoan is (exploration),
I want to mention a few points about privacy when dealing Balbtkoan.
If Alpetkoan entered through a network (Tor) that hide the IP address of thy,
You can use Alpetkoan without showing anything other than the public key.
To avoid the one to track all your transactions
(Remember, all transactions are stored on all computers!)
You can generate a new public key for each incoming deal.
However it can be linked to these public keys accidentally.
In the deal we have shown previously used six other deals as sources of money,
And that with all these inputs received to different addresses
They are all linked to the transaction.
And the sender has demonstrated its ownership of all these titles
Through the provision of electronic sign necessary to decode the lock each.
The researchers used these links to study user behavior currency Alpetkoan.
You may think that generate a public key to receive the funds may eventually lead to reveal the true identity,
But even this step are confidential.
And it can be done without an internet connection!
Where simply press the custom button in the wallet program
And the software will generate a public key and a special two new.
Since there are many possibilities for these titles,
There is no need to make sure that no other person has the same title.
Compare this with the registration service for e-mail
Where most of the names that you might consider them to be used in advance.
In fact, if you can guess someone else will own all his money key!
This is the number of all possible possibilities for addresses Alpetkoan.
These massive numbers in several ways to protect Alpetkoan system.
And it is useful to try to imagine the extent of magnitude,
Some estimated the number of grains of sand on Earth by 7.5 million trillion,
Now imagine that every grain of sand is another land full containing other sand,
With this figure will remain much lower than the number of possibilities Alpetkoan addresses.
Flanl_khas what we have learned about Alpetkoan security now.
By ensuring the validity of the electronic signature.
We know that the rightful owner is the only one capable of sending the deal
To verify that the sender has enough money to spend.
Check every income indicated to make sure that it is not an expense
But there is still one loophole in the system
This makes “verify that the transaction is disbursed” is not trusted.
And this gap related to the order of the transaction.
As the transaction moves from one node to another over the network,
There is no guarantee that the order in which these deals received is the same as the order in which it was established.
Do not trust registered on the transaction time
Because the owner of the deal can easily lie about the time of the establishment of the deal.
And therefore we have no way to know whether a transaction was established before the other
This opens the door to fraud.
A user can be cunning like Alice sends a deal that sends them his money to Bob,
Bob and then wait until the goods shipped to him,
And then sends another deal which refers to the same intake and return the money to himself.
Because of the differences in the speed of transmission of the message,
You will receive some of the network nodes in the second letter (in which the money was transferred to itself)
Before the message where the money is spent on Bob.
And when you reach the deal with Bob would be considered illegal
As it tries to re-spending one earnings.
Bob Vijsr this both of his goods and his money.
The result would be contrary to within the network whether or not Bob owns this money
Because of the absence of a way to prove that one of the deals came first.
And therefore there must be a way to allow for the entire network to agree on the order of a transaction,
And it is complex in a decentralized system.
The solution in the Alpetkoan system is a smart way to ensure the protection and determine the order of occurrence of transactions
And through some kind of racing sports.
Arranges Alpetkoan system deals placing them in groups called blocs,
And then connects these blocks with each other in so-called chain blocks.
Note that it is different from the chain of transactions that we talked about previously.
Where he used a series of blocks to arrange deals,
While serving the chain of transactions to track the ownership of the funds.
It is noteworthy in each block to the previous block,
And this is what makes it one of the blocks other precedes chronologically.
Where you can keep track of these signals about the past until you reach the first mass of transactions occurred.
Ntabbar that deals in one block occurred at the same time.
And called the deals that did not fall within the block after transactions is ranked or undocumented.
Any node can be several deals not documented in the mass rally
Then it suggests this block on the rest of the nodes in the network to be the new cluster in the chain.
Because several people can establish several blocks at the same time,
There are several possible new options as a bloc.
How can the network to decide which blocks are the next in the series?
We can not rely on the order of receipt of the blocks,
As we explained earlier for deals,
These blocks can reach different in the different nodes in the network order.
Part of the solution is that each block must contain a distinctive mathematical solution to the issue.
Where computers are used text content in the cluster to add random numbers Speculative
To create the so-called “retail encrypted”
Until you find the result is less than a specified value.
Continued retail creates short as a result of any text, whatever its length,
In our case the result is a record length of 32 bytes.
Here are some examples of retail user continued in Altbekoan SHA256 system
Notice how much output changes after adding one point at the end of the third example.
No one can predict the output never
Consequently, the only way to find a particular output is to carry out a random guess.
This is like trying to guess the password to lock.
You may be lucky in the first attempt,
But you need a few guesses average.
In fact, it may take a normal computer a few years to find true guesswork solves mass.
All computers operate on a network Alpetkoan to guess the numbers,
And thus find the solution takes an average of ten minutes.
Broadcast the first to find a solution to the issue of mass mathematics
And group transactions contained therein will become a new block in the chain.
Random sports issue lead to a variation of the times when people find a solution
Which reduces the probability to find two to resolve the issue at the same time.
But several blocks at the same time may sometimes be resolved
Which leads to the presence of several possible branches.
In this case, you have to build on the first block you receive.
Others may receive the blocks in a different order
And each of them will be built on the first block received.
And this node resolved when someone resolves the next block.
And the base should always rely longer series are available.
Make the possibility of solving math blocks at the same time weak.
The probability of occurrence of several consecutive times weaker.
And the result is that a series of blocks settle down quickly,
This means that all agreed on the order of the blocks added to the end of the chain.
Ambiguity at the end of the chain a significant impact on security transactions.
For example, if you signed your deal in the short section in the series will lose its place in a series of blocks.
This means that they will return to box undocumented transactions,
It later becomes a new block components.
Unfortunately, the deal opens up the possibility of losing their place in the chain to the door to the spending multiplier attack
Which was the first reason we invented a system arrangement.
Let’s see how it works spending multiplier attack in the system that described now.
The conman (Alice) to send money to Bob.
Bob is expected to document the deal in a series of blocks and then ship the goods.
Now, and because the contract always choose the longest chain,
If it can not generate the longest series in which the deal is replaced with Bob another deal with someone else,
Erased his money from the chain.
Bob will return a deal in principle to non-documented transactions.
But since the deal is not replaced it with another which has spent the same intake,
Bob contract deal will be considered invalid, because they rely on income already spent.
How prevents the ranking system is not fool Bob?
You may think that you can not pre-calculated series of blocks to the proposed network in a timely manner,
But sports matter in each block to prevent such.
Should we look more deeply on the encrypted hash continued that we talked about in advance in order to understand exactly why.
As I mentioned previously,
Cluster solution depends on trying to make the encrypted hash of the block output of less than a certain value.
And do so through the experience of different random numbers at the end of the block.
And output becomes a sign marked after be found this block (fingerprint).
And change one character in the cluster will make retail output completely different,
And so as we saw earlier when we add point.
Using retail output, or footprint, to refer to the previous block.
And therefore it can not replace the block in the middle of the chain because the hash value of the new block will vary,
And the signal in the next block will not refer to it later.
And the output is self-evident, but more importantly, one can not solve the block before we solve the bloc that precede them.
And the reference to the previous block is part of the cluster text that enters the retail continued,
And any change in it will need to be re-solution again.
And to return to Alice,
We are not aware can not calculate a branch in advance.
You can begin to dissolve the block only if the cluster that you want to build on it Solved, and the retail value of the known.
And therefore they are in a race with the rest of the network until the goods shipped Bob,
And it is the time you want it not display the longest branch.
And ask the question last one
And you are Can not precede all if you own a computer supernatural speed,
Or perhaps full of computer room.
Even if possessed thousands of computers will not be able to profit from the race and mass solution,
Because they do not race alone computers,
But it raced the entire network.
This is like a lottery game.
Can use thousands of computers,
Or to buy thousands of lottery cards,
But even if it did, the possibility of profit for someone else remains high.
It has to have more than half of computational power for the entire network
To be her chance to dissolve the bloc by another person 50%.
And it should have much more in order to have the possibility to solve several sequential blocks before the rest is greater.
Protect deals in the series of blocks through a sports race,
This race puts forward against the rest of the entire network.
And result in the creation of new blocks over the old that the old blocks in the chain more secure.
And the attacker must be preceded by the network for longer
To succeed spending multiplier attack by replacing old ones block.
The system exhibition spending multiplier attack near the end of the series,
For this reason is advisable to wait until added a few new blocks
Before it is considered the process of receiving final funds.
One final note series blocks before I begin to explain another issue for Alpetkoan system.
What is surprising that all the above and I explained does not need any confidence.
If you receive information from strangers on the network,
You can be sure that the blocks yourself solutions are correct.
Because tough math problems, you are sure that there is no striker is able to manufacture himself.
The existence of solutions proved to be caused by the computational capacity of the entire network.
After that we talked about the mechanism of sending money through digital signature and chains deals,
How protects the order of these deals in a series of blocks,
Let’s talk about another topic: where it comes from coin Alpetkoan?
You have to refer to an old deal where you’re the recipient before you can send money,
But how these funds enter into the ownership chain at the beginning?
The way through which generate and distribute the pieces at random,
Award is to give each of finding a solution to the mass.
For this so-called solution blocks “prospecting”
With the primary aim is to document transactions and protect the chain blocks.
Cut the prize every four years to half and in the end will not be created any new cut,
There will be about 21 million pieces in the end.
Remember that you can send the equivalent part of a million percent portion of the piece,
And thus the limited number of pieces on our ability to use it will not affect.
When the distribution of the awards depends,
What are the incentives that will pay prospectors to handle deals?
You can prospector receive with their prize any fees on deals
Which can optionally be present within these transactions.
Prospectors currently adds deals without fees in the blocks
Because their primary goal is the prize after a mass solution,
In the future, transactions will be dealt with mostly by fees attached to them,
The deals that do not carry fees Vsijahlunha often.
And therefore will not be sending money in free Alpetkoan,
But we hope to be cheaper than the fees levied on credit cards.
As I mentioned earlier, it would take a normal computer and the average number of years to resolve the block,
And thus the chance of one individual to resolve any block before the rest of the network (which normally takes ten minutes) is very low.
For a stable financial Ward,
Many people join groups called Mines
Which cooperate to solve the mass and resources are distributed based on the amount of participation.
And is similar to that lottery cooperative groups,
Except that some of these mines is very large, and make up more than 20% of the computers on the network.
The presence of these large mines have a significant impact on safety.
As we mentioned earlier, one attacker can not solve a series of sequential blocks before the rest of the network,
But this becomes possible, and the probability of its occurrence increases the more computing capacity of the attacker compared with the rest of the network.
And it has already managed one of the mines, union Alpetkoan, to replace the six blocks of sequential alone,
It identifies the number of its affiliates voluntarily and in order to prevent the collapse of confidence in network Alpetkoan.
Even with a high computing power,
Whenever the deal earlier in the series, the more change more difficult by the attacker.
Currently it recommended that you wait for one block, or get a closer one, before the transmission is considered final.
And for the great deals, wait six blocks at least.
And with the ability of union Alpetkoan six sequential blocks solution you’ll probably have to wait more.
The blocks are designed so that you need ten minutes to solve,
So you have to wait a full hour to solve 6 new blocks.
If you compare it with the few seconds it takes to send a deal via credit card,
You’ll find all this waiting period to document the deal is troublesome,
But remember that credit card users can call steal their card after several months
And to restore their money from the merchants,
And therefore Alpetkoan much faster than the point of view of the merchant.
The choice of ten minutes was randomly,
But too little will lead to instability,
And long time will lead to the postponement of documenting transactions.
And join with the largest number of computers to the network,
With the hardware design software dedicated to the exploration,
Will decrease the time needed to resolve the block.
And to compensate for it,
Re-evaluation of all programs Alpetkoan difficult math problems every two weeks
So it takes ten minutes to solve.
Conversely, there is another digital currency called the Aatkoan was able to operate time of 2.5 minutes for each block.
In summary, Alpetkoan is a digital coin protected mathematics
And it works to save users on the network.
The digital signature gives individuals the right to conduct transactions,
And transferred ownership across the chain of transactions,
And saves the sequence of occurrence of transactions arranged in a series of blocks.
And a request to resolve the issue of mathematics for each block,
Put the attackers in the competition can not be Arbhoha against the rest of the network.
The future Alpetkoan many creative ideas,
Such as preventing government intervention and reduce financial secrecy and transfer fees.
There are many challenges faced, such as the difficulty of sharing Alpetkoan with other currencies,
And was a classification refuge for illegal acts and tax evasion,
So governments may try to prevent them.
In addition, the mathematics race series which protects the blocks consumes a large amount of electricity.
If you want to read a written copy of the video
You can drop my blog,
imponderablethings.com
The Code contains additional explanations for the underlying mathematics behind the digital signature and encrypted hash that support the system.
Please follow and like us:
Be First to Comment